Download
Here you will find the basic information to download and install Carbonio CE
Compatible Operating Systems
The following operating systems are compatible with Carbonio CE
| Operating system | Version |
| Ubuntu | -20.04 LTS -22.04 LTS |
| Red Hat | -8 -9 (Beta) |
Hardware requirements
The following are the minimal recommended physical resources to install Carbonio CE
| Operating system | Version |
| CPU | 64-bit processor, +6 cores vCPU |
| Memory | 32 Gb RAM |
| Disk space | 50 Gb for system + mail storage |
Installation scripts
These are the repositories in order to install Carbonio CE
| Operating system | Script |
| Ubuntu 20.04 | wget https://repo.zextras.io/release/ubuntu |
| Ubuntu 22.04 | wget https://repo.zextras.io/inst_repo_ubuntu.sh |
| Red Hat 8 | wget https://repo.zextras.io/release/rhel8 |
| Red Hat 9 (Beta) | wget https://repo.zextras.io/release/rhel9 |
Installation process
For simplicity, we will show the installation for a single-server instance on Ubuntu 22.04 LTS
Is important that you understand that Carbonio CE has 12 different roles that can be installed on a single node (single-server) or more nodes (multi-server).
1. MTA (Mail Transfer Agent):
- The following ports shall be open:
- 25/TCP (SMTP): Receiving incoming emails between servers.
- 465/TCP (SMTP sobre TLS): Sending emails with TLS.
- 587/TCP (SMTP autenticado): Sending authenticated emails requires STARTTLS.
2. Proxy:
The following ports shall be open:
- 80/TCP (HTTP): Unsecured connection to Carbonio web client, redirected to https.
- 110/TCP (POP3): External POP3 services.
- 143/TCP (IMAP): External IMAP services.
- 443/TCP (HTTPS): Secure connection to the Carbonio web client.
- 993/TCP (IMAPS): External secure IMAP access.
- 995/TCP (POP3S): External secure POP3 access.
- 5222/TCP (XMPP): Required by the Work Stream Collaboration (Chat) role.
- 6071/TCP (HTTPS): Secure access to the Administration Panel.
3. VideoServer:
- These ports shall be used for Video server
- 20000-40000/UDP: Client connections for audio and video transmissions.
The following ports are required to be open internally by Carbonio CE
On each node:
- The following ports shall be open on each node:
- 22/TCP (SSH): SSH access for administration.
- 8301/TCP y UDP: Managing the Gossip protocol on the LAN.
- 9100/TCP: Data exporter for Carbonio Monitoring Node.
- 9256/TCP: Process exporter for Carbonio Monitoring.
4. Postgres:
- The following ports shall be open on each node:
- 5432/TCP: Access to the Postgres database.
- 9187/TCP: Exporting data from Postgres for Carbonio Monitoring.
5. Directory Server:
- The following ports shall be open on each node:
- 389/TCP: Insecure LDAP connection.
- 636/TCP: Secure LDAP connection.
- 9330/TCP: Exporting LDAP data for Carbonio Monitoring.
6. MTA:
- The following ports shall be open on each node:
- 25/TCP (SMTP): Receiving incoming emails.
- 465/TCP (SMTP sobre TLS): Sending emails with TLS.
- 587/TCP (SMTP autenticado): Sending authenticated emails requires STARTTLS.
- 7026/TCP: Milter service link address.
7. Mailstore and Provisioning:
- The following ports shall be open on each node:
- 7025/TCP: Local mail exchange using the LMTP protocol.
- 7071/TCP: SOAP services communication.
- 7072/TCP: NGINX Discovery and Authentication.
- 7073/TCP: SASL Discovery and Authentication.
- 7110/TCP: Internal POP3 services.
- 7143/TCP: Internal IMAP services.
- 7993/TCP: Internal secure IMAP access.
- 7995/TCP: Internal secure POP3 access.
- 8080/TCP: Access to internal HTTP services.
- 8443/TCP: Internal HTTPS services.
- 8735/TCP: Internal mailbox communication.
- 8742/TCP: Internal HTTP Services, Advanced Module.
- 8743/TCP: Internal HTTPS services, advanced module.
8. VideoServer:
- The following ports shall be open on each node:
- 8090/TCP: Servlet communication.
- 8188/TCP: Internal connection.
9. Proxy:
- The following ports shall be open on each node:
- 9113/TCP: Exporting nginx data for Carbonio Monitoring.
- 11211/TCP: Access to memcached.
10. Carbonio Mesh:
- The following ports shall be open on each node:
- 8300/TCP: Managing incoming requests from other agents.
- 8302/TCP y UDP: Gossip protocol management on the WAN.
- 9107/TCP: Exporting data from Carbonio Mesh to Carbonio Monitoring.
- 21000-21255/TCP: Range for sidecar service registration ports (automatically assigned).
Make sure to take the appropriate security measures for these ports. We will need at least one public IP associated with an A record such as mail.domain.com and an MX record that corresponds to the A record, for example domain.com. We must also implement SPF, DKIM and DMARC records to improve security. It is also necessary that there are no IPv6 entries in our hosts files. If we are going to install several servers with several nodes, we must have a clear architecture from the start to name these nodes and make our lives easier in the future, for example:
proxy1.domain.com is the (first) proxy node
mta1.domain.com is the (first) MTA node If you expand this role, the following would be:
proxy2.domain.com becomes the second proxy node
mta2.domain.com becomes the second MTA node. You can easily install Carbonio CE on a single node using the script provided by the developer.
In order to start the installation, run the following commands to add the Carbonio repositories.
sh -c ‘echo “deb [arch=amd64 signed-by=/usr/share/keyrings/zextras.gpg] https://repo.zextras.io/release/ubuntu jammy main” > /etc/apt/sources.list.d/zextras.list’
wget -O- “https://keyserver.ubuntu.com/pks/lookup?op=get&search=0x5dc7680bc4378c471a7fa80f52fd40243e584a21” \ | gpg –dearmor | sudo tee \ /usr/share/keyrings/zextras.gpg > /dev/null
chmod 644 /usr/share/keyrings/zextras.gpg
sh -c ‘echo “deb https://apt.postgresql.org/pub/repos/apt $(lsb_release -cs)-pgdg main” > /etc/apt/sources.list.d/pgdg.list’
wget -O- “https://www.postgresql.org/media/keys/ACCC4CF8.asc” | \ gpg –dearmor | sudo tee /usr/share/keyrings/postgres.gpg > \ /dev/null
chmod 644 /usr/share/keyrings/postgres.gpg sed -i ‘s/deb/deb [signed-by=\/usr\/share\/keyrings\/postgres.gpg] /’ /etc/apt/sources.list.d/pgdg.list
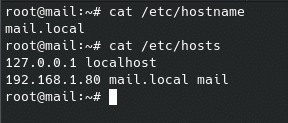
After you run apt-get update and have set the repositories, you will need to download the installation script from Here. Mind that before launching the script, your hostname and hosts file need to have the full name with the domain, otherwise you will get “service-discover: error: invalid binding address selected” error, and thus producing the following errors: service-discover: error: unable to open /etc/zextras/service-discover/cluster-credentials.tar.gpg. To avoid this, you will need to modify manually both files:
hostnamectl set-hostname mail.yourdomain.com
echo -e “127.0.0.1 localhost\n192.168.1.80 mail.yourdomain.com mail” > /etc/hosts. In case you are installing for test purposes, it is mail.local, but if you do it with a real domain, you will have mail.yourdomain.com.
Then you will need to give execution permissions with chmod +x install_carbonio_ce_singleserver_ubuntu.sh and then executed it. ./install_carbonio_ce_singleserver_ubuntu.sh. The installation will take some minutes depending on your resources and internet connection. While installing, the system will ask you for the public IP of the video server, where in this case is 192.168.1.80

When the script finishes, it will display the passwords of Carbonio Mesh and PostgreSQL services. You should save it in a secure place to not forget.

To finish, you will change the password of the default user (zextras@yourdomain.com), with the following command:
su – zextras -c “carbonio prov setpassword zextras@yourdomain.com new_password”. Consider that if you are it in a test environment like ours where our domain is only local, the user will be zextras@local, that is, only the domain part Once this is done, we can access the administration panel through port 6071
